Technology changes so quickly, everyday apps are being updated and gaining new features. Here are some tech tips from our IT Support team and new features to help you get the most out of your technology.
Are you a serial tab opener, or tab collector - 100 tabs open across multiple Google Chrome windows only to never be able to find the one you're looking for so you just open another new tab? I'm guilty of this! Google has recently released a great tech hack - a management system for tabs, meaning you can group tabs together, label and color code them. Getting started is easy:
1. Check you have the most up to date version of Google Chrome installed
2. Right click a tab and select 'add tab to new group'
3. Give the group a name and color
4. Right click another tab
5. Hover over 'add to group'
6. Select add to new group, or select an existing one from the list
Have you ever closed a tab only to realise in that instant you still need it? I do this all the time! You can quickly re-open that tab by pressing Control + Shift + T, such a life saver!
Unroll me is an app that will instantly provide you with a list of all your subscription emails, giving you an easy way to unsubscribe, this handy tech hack is free and a great way to kick off spring cleaning your computer.
If you are hosting a meeting with 5 or more participants, you can start your video meeting all together, then break them out into rooms. Our IT support team is spread between Melbourne, Sydney and Brisbane, this new feature has been very helpful for our cross border meetings, here's how it works:
1. Make sure you have the 'Turn on new meeting experience' selected in the General Settings of your Teams profile
2. In your meeting, using the menu along the top click the breakout icon
3. You have the option of manually or automatically assigning which participants are grouped together, and across how many rooms
4. When you are ready for the breakout rooms to start simply click Start rooms to open them
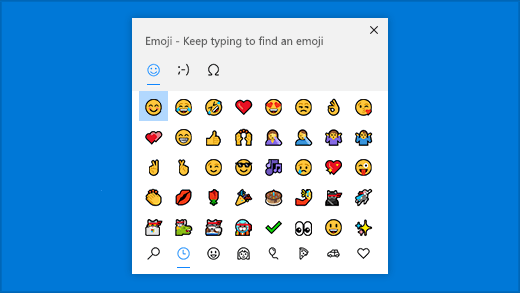
Hooray, I have been waiting for this day to come, as someone who writes content and often googles 'tick emoji' to copy and paste it into content, I am very excited to see emojis built natively into Windows. Here's how you can access them:
1. Make sure you have the latest version of Windows installed + Windows updates, this is a new features so if you're not up to date it is likely you won't see it.
2. Press the windows key + . on your keyboard to open the emoji panel. You can also use kaomojis to create faces with text and symbols.
Have you seen our free guide to maintaining your computer? Download it today to learn how to make your computer run faster (and safer).
What is Microsoft Teams? Microsoft Teams is a valuable workplace tool, keeping employees connected and organised. It drives productivity and […]
Read moreStaying ahead of the technological curve in today’s fast paced landscape is essential. The concept of engaging a vCIO has […]
Read moreWho Are Play Ransomware? Play is a group of hackers that are responsible for extortion and ransomware attacks on government […]
Read more

























4 Gipps St, Collingwood VIC
+61399276000
U18, 23-31 Bowden Street, Alexandria NSW
+612821428855
Unit 1, Building 6, 2404 Logan Rd,
Eight Mile Plains QLD
+61731371313